What attacks are old Wi-Fi adapters suitable for?
A question was asked on the forum, is it possible to use very old adapters that only support modes b and g to audit the security of Wi-Fi networks? It seems that these adapters are already completely useless for attacking wireless Wi-Fi networks, but in reality this is far from the case!
I found a couple of ancient Wi-Fi adapters at my place:
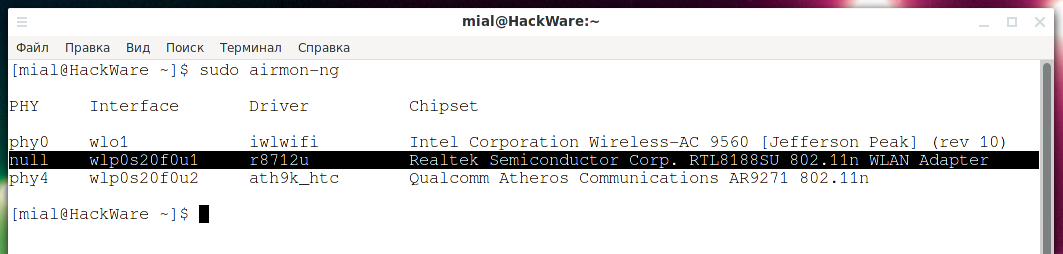
- Upvel, Model No: UA-213WNU. Airmon-ng is defined as “Realtek Semiconductor Corp. RTL8188SU 802.11n WLAN Adapter” with r8712u driver
- D-Link, Model No: DWA-110. In airmon-ng it is defined as “D-Link System DWA-110 Wireless G Adapter (rev.A1) [Ralink RT2571W]” with rt73usb driver
Moreover, Upvel has a detachable antenna, so instead of the standard one, I screwed on a larger antenna.
And D-Link has a suspiciously hot metal contact, which is inserted into the USB connector, so, by the way, be careful with old equipment.
How popular are Access Points on Wi-Fi standards b and g so far?
Access Points on b and g are currently an exception, meaning they are practically non-existent. But, in fact, it's too early to give up – there are plenty of attacks that simply do not depend on the standards used, or are possible due to the backward compatibility of the new standards with the old ones.
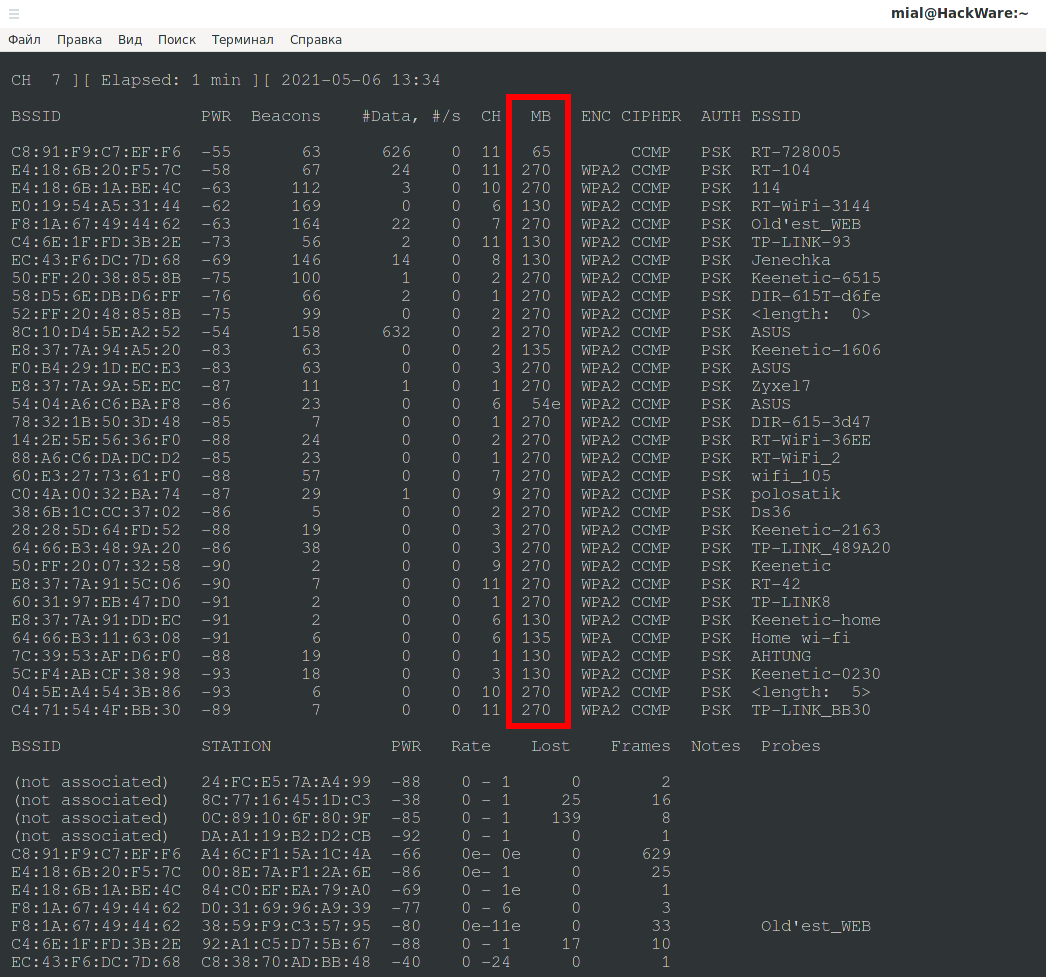
How to find out in Airodump-ng on which Wi-Fi standard (b, g, n, ac) the Access Point works
You can find out which standard the AP supports by such an indirect indicator as the data transfer rate. Airodump-ng shows the transfer rate in the MB column.
MB is the maximum speed supported by the AP:
- If MB = 11, it is 802.11b,
- If MB = 22 is 802.11b+,
- If this field is 54, then it is 802.11g.
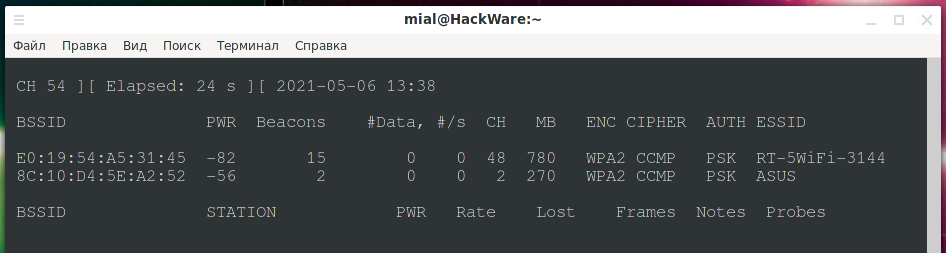
- Speeds up to 300 (65, 130, 135, 270) mean it's 802.11n.
- 802.11ac has speeds up to 1300 Mbps at 5 GHz plus up to 450 Mbps at 2.4 GHz.
- The period (after the digit) means short preamble support, “e” indicates the network has QoS enabled (802.11e).
If you do not understand something in the subsequent commands, then for an explanation of them, see the article “Linux Wi-Fi Cheat Sheet: Tips and Troubleshooting”.
We turn off programs that may interfere with our activity:
sudo systemctl stop NetworkManager sudo airmon-ng check kill
We set the wireless network interface to monitor mode:
sudo ip link set wlp0s20f0u2 down sudo iw wlp0s20f0u2 set monitor control sudo ip link set wlp0s20f0u2 up
Run Airodump-ng to view information about Access Points:
sudo airodump-ng wlp0s20f0u2
There are only 1-2 APs next to me with a speed of 54 Mbps. That is, there are few APs working on the g standard, but there are no APs on the b standard at all.
Mostly the standard n is used.
I still found the ac standard at 5 GHz:
To turn off monitor mode and return the Internet connection, execute:
sudo ip link set wlp0s20f0u2 down sudo iw wlp0s20f0u2 set type managed sudo ip link set wlp0s20f0u2 up sudo systemctl start NetworkManager
Drivers for old Wi-Fi adapters
The adapter on the RTL8188SU chipset is not seen by the iw command. And airmon-ng shows null as PHY.
The problem seems to be the missing driver. At the same time, NetworkManager can use this adapter and even connected to the AP. The “ip a” command also sees the adapter and the IP addresses assigned to it.
The driver was found here: https://github.com/chunkeey/rtl8192su, but it cannot be compiled on kernels > 4.14. Then a fix was posted here https://github.com/luks3n/rtl8192su. But currently, on the latest versions of the Linux kernel, this driver again fails to compile due to an error.
When trying to put it into monitor mode, I was getting errors:
sudo iw wlp0s20f0u1 set monitor control command failed: No such device (-19)
Using the iwconfig command:
sudo iwconfig wlp0s20f0u1 mode monitor
Error for wireless request "Set Mode" (8B06) :
SET failed on device wlp0s20f0u1 ; Invalid argument.
In general, for attacks that do not require switching to monitor mode, this adapter is suitable, but it is not possible to switch it to monitor mode (if the driver supports it at all).
Let's put it back in place (it works fine on an old computer with Windows 10) and move on to an even more outdated model based on the Ralink RT2571W chipset, this model does not even have support for the n standard, only g, so it is of interest to us in the first place. This adapter worked right away, no drivers needed to be installed.
Pixie Dust Attack
In theory, WPS does not depend on standards, so the Pixie Dust attack and full brute force attack of WPS pins should work. I checked – yes, indeed the adapter with support for the G standard was able to crack the PIN and password of Wi-Fi networks.
And it makes no difference whether your old adapter supports monitor mode, see the article “How to hack Wi-Fi with a regular adapter without monitor mode” for details.
Capturing handshakes
YES! Possible!!! I was sure that this is the attack that the adapter will not be able to carry out. I used the method from the article “Automatic capturing of handshakes with Besside-ng” and in a couple of minutes I had 3 handshakes from APs working on the N standard, although the adapter does not support anything higher than G.
Checking against the 3WiFi database
There is no wireless adapter requirement for this attack, so it works as well. For details, see the article “How to get passwords of Wi-Fi hot-spots nearby (without monitor mode)”.
Gathering Information about Access Points
Do not think that if the wireless adapter does not support any of the standards, then it will not be able to see the Access Points operating on this standard. This is not true.
Legacy adapters that do not support anything above the g standard can see all APs and gather information about them. Except, of course, those that run at 5 GHz.
If your Wi-Fi adapter supports monitor modes, then you can use the Airodump-ng program.
Otherwise, see the article “How to scan wireless networks with a regular Wi-Fi adapter”.
Conclusion
In principle, this is the end of the article – if an outdated adapter supports client deauthentication and handshake capture, and also supports an attack on WPS, then we can state that outdated adapters support any attacks that can be performed by modern Wi-Fi adapters. Except, of course, for 5 GHz attacks.
Apparently this is due to the fact that the standards affect only the data transfer rate and do not affect the authentication protocols. Or it is due to the backward compatibility of the new standards with all the old ones.
See the Wireless section, which contains all the material on auditing the security of Wi-Fi networks: https://miloserdov.org/?cat=2
If you need a modern Wi-Fi adapter with large antennas, support for 5 GHz, AC standard and monitor mode, then you can find the list here.
Related articles:
- How to increase TX-Power of Wi-Fi adapters in Kali Linux (51.6%)
- USB Wi-Fi Adapters with monitor mode and wireless injection (100% compatible with Kali Linux) 2022 (51.6%)
- How to install the Realtek RTL8821CE driver (51.6%)
- An easy way to increase TX Power for Wi-Fi in Kali Linux and BlackArch (51.6%)
- Alfa AWUS052NH – Kali Linux Compatible USB Adapter (50%)
- How to hack Wi-Fi using Reaver (RANDOM - 18.1%)