What is Bluetooth Low Energy (BLE) and how to hack it
Bluetooth Low Energy (BLE) is a part of the Bluetooth 4.0 specification which additionally also includes Classic Bluetooth and Bluetooth High Speed Protocols. Compared to classic Bluetooth, BLE is intended to use lesser power while maintaining similar communication range. BLE is an ‘always off’ technology and only transmits short amounts of data when required. This significantly reduces power consumption making it ideal to use in cases where a persistent long term connection is required with a low data rate. BLE is perfect for a TV remote but not for a wireless media streaming device which needs a large amount of data to transmit.
How to Hack Bluetooth Low Energy (BLE)
By its concept, BLE is a simplified version of Bluetooth, which does not hop channels (does not change frequencies operating on), which facilitates sniffing and a man-in-the-middle attack. BLE does not have a built-in security protocol. The implementation of BLE security is entrusted to manufacturers of end devices that do not always approach this in good faith. For this reason, many BLE devices can be easily discovered at almost any time during their operation. However, often they do not contain any mechanisms to limit reading and even writing to them, that is, they are open to anyone to connect and modify.
The essence of the Bluetooth Low Energy hacking process can be described in the following stages:
- Device discovery
- Reading its Services and Characteristics
- Detection Writable Characteristics
- Mapping Characteristics ID to its functions
- Change Characteristic Values
The fourth stage is the most creative and the most difficult. Sometimes the meaning of Characteristics IDs can be found in the documentation for developers. Sometimes you have to perform Fuzzing against the values and see what will change. The most difficult way is reverse engineering the intercepted Bluetooth traffic or reverse engineering of device management application.
I will show an example of changing BLE Characteristics on a device using bettercap.
Run bettercap:
sudo bettercap
We type the command to enable the module for detecting BLE devices:
ble.recon on
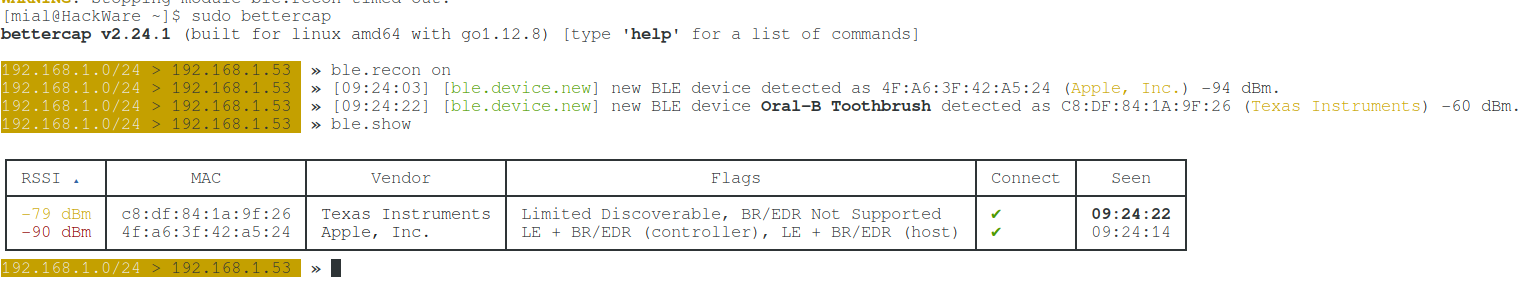
When new devices are detected and if the devices are lost, approximately the following messages will be displayed:
192.168.1.0/24 > 192.168.1.53 » [06:46:17] [ble.device.lost] BLE device Oral-B Toothbrush C8:DF:84:1A:9F:26 (Texas Instruments) lost. 192.168.1.0/24 > 192.168.1.53 » [06:49:29] [ble.device.new] new BLE device JBL Flip 3 detected as B8:D5:0B:E2:21:88 (Sunitec Enterprise Co.,Ltd) -77 dBm. 192.168.1.0/24 > 192.168.1.53 » [06:50:02] [ble.device.lost] BLE device JBL Flip 3 B8:D5:0B:E2:21:88 (Sunitec Enterprise Co.,Ltd) lost. 192.168.1.0/24 > 192.168.1.53 » [06:50:35] [ble.device.new] new BLE device detected as 7C:F1:1F:E7:B1:C1 (Apple, Inc.) -82 dBm. 192.168.1.0/24 > 192.168.1.53 » [06:51:07] [ble.device.lost] BLE device 7C:F1:1F:E7:B1:C1 (Apple, Inc.) lost. 192.168.1.0/24 > 192.168.1.53 » [06:57:55] [ble.device.new] new BLE device Oral-B Toothbrush detected as C8:DF:84:1A:9F:26 (Texas Instruments) -64 dBm.
To display devices that are currently within reach, run the command:
ble.show
To show the characteristics of a specific device, run the command of the following form, where instead of the MAC, specify the MAC address of the device:
ble.enum MAC
For example, I'm interested in the device C8:DF:84:1A:9F:26:
ble.enum C8:DF:84:1A:9F:26
Common Attributes Protocol (GATT)
Using a common data protocol, known as an attribute protocol, GATT determines how two BLE devices communicate with each other using concepts such as service and characteristic. This protocol saves all services and features in a lookup table using 16-bit identifiers, as indicated in the Bluetooth SIG. It is important to note that the GATT is initiated only after the GAP-regulated Advertising process is completed.
The two main concepts that make up the GATT
- Services
- Characteristics
Services
Services can be represented simply as a cabinet in which there can be many boxes, which in turn are called characteristics. A service can have many characteristics. Each service is unique in itself with a universally unique identifier (UUID), which can be 16 bits for official adapted services or 128 bits for custom services.
Characteristics
Characteristics are the most fundamental concept in the GATT transaction. Characteristics contain one data point and are similar to services, each characteristic has a unique identifier or UUID, which differs from another characteristic.
Here are the SIG specifications for characteristics and services for BLE devices. Any BLE device that has officially accepted the UUID from SIG must use the identifier specified by them in their applications.
For example, the official UUID of transmit power (TX power) in accordance with the SIG mandate is 0x1804.
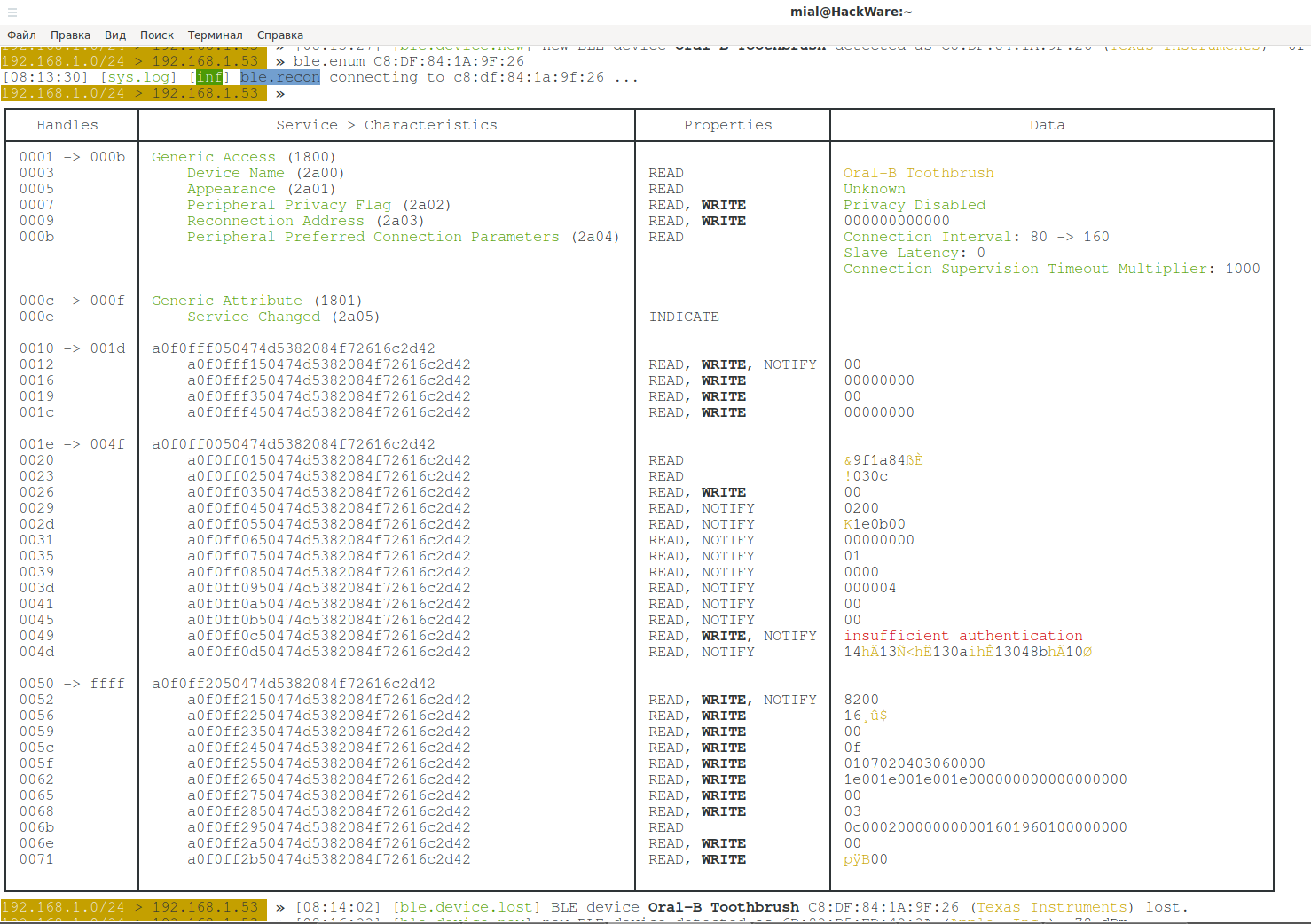
In the screenshot above, “Generic Access (1800)” is a 16-bit service. Inside this service, the following 16-bit characteristics:
Device Name (2a00) Appearance (2a01) Peripheral Privacy Flag (2a02) Reconnection Address (2a03) Peripheral Preferred Connection Parameters (2a04)
Another 16-bit service is Generic Attribute (1801), it contains only one 16-bit characteristic: Service Changed (2a05).
Next are three 128-bit services, the first of which is “a0f0fff050474d5382084f72616c2d42”, contains four 128-bit characteristics:
a0f0fff150474d5382084f72616c2d42 a0f0fff250474d5382084f72616c2d42 a0f0fff350474d5382084f72616c2d42 a0f0fff450474d5382084f72616c2d42
There is a problem in identifying services and characteristics. For 16-bit services and characteristics, everything is simple, links to their values are given above. As for 128-bit services and characteristics, each vendor may have their own ID. That is, you need to make some efforts to map, for example, something like d0611e78-bbb4-4591-a5f8-487910ae4366 with something like the Apple Continuity Service. For mapping, you can use at least two approaches:
- analysis of the device management application (many devices have Android programs)
- fuzzing – entering various data and monitoring the device, what has changed in it
In the Properties column, you will see the properties of this characteristic, they can be:
- READ
- WRITE – we can alter the value of this characteristic
- NOTIFY
- INDICATE
The Data column contains the current value of the characteristic, or additional information, for example:
insufficient authentication
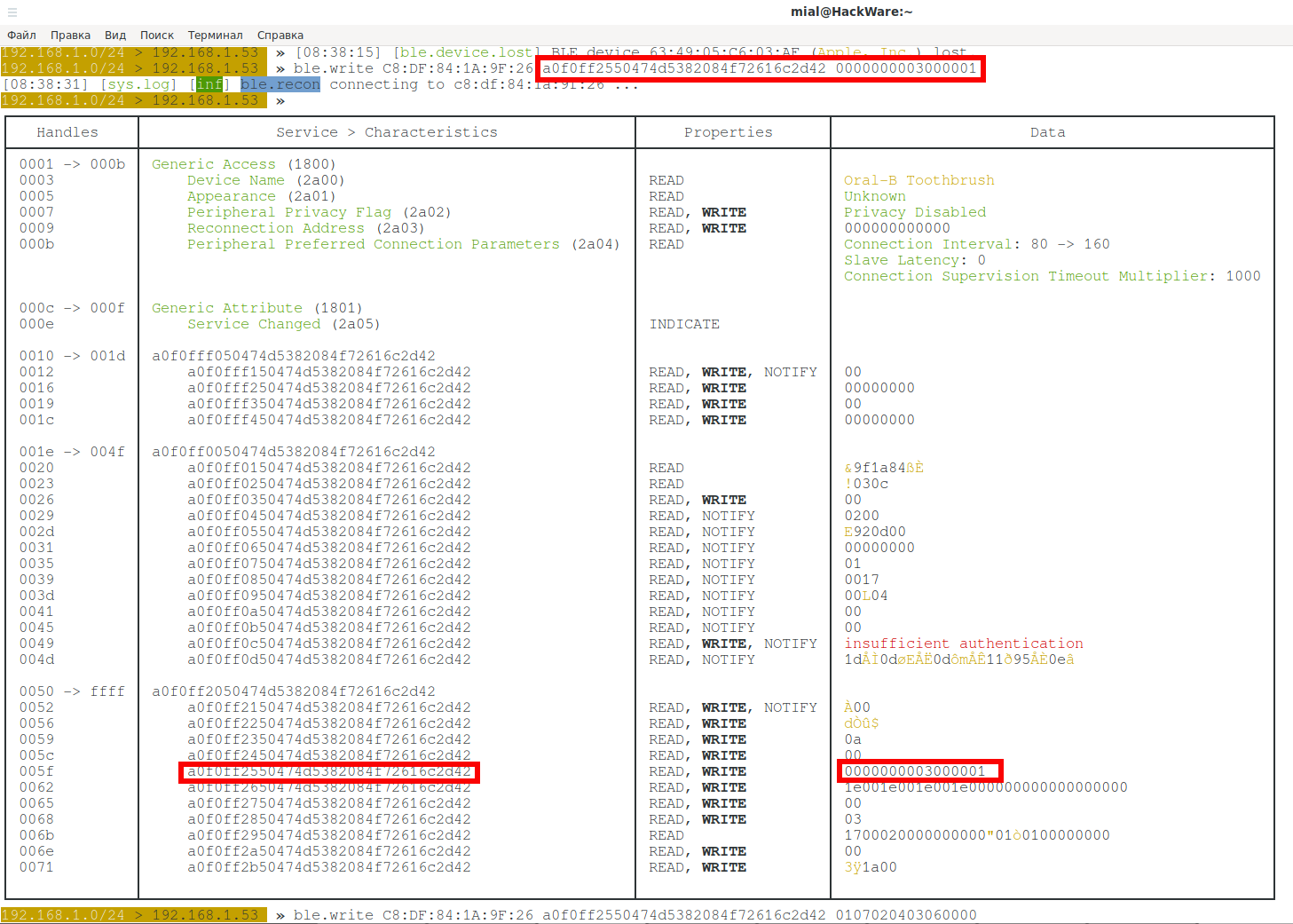
To write HEX_DATA data to a BLE device with the specified MAC address, in the characteristic with the UUID:
ble.write MAC UUID HEX_DATA
Command example:
ble.write C8:DF:84:1A:9F:26 a0f0ff2350474d5382084f72616c2d42 11
To achieve aims, it is necessary to to know what the characteristic IDs mean. Here is an example of the values for my device – this is an Oral-B Genius 9000 electric toothbrush (by the way, I recommend it). The value of the characteristics I found on the Internet.
Service a0f0fff050474d5382084f72616c2d42
a0f0fff150474d5382084f72616c2d42 (Command)
properties read, write, notify
value 00 | ''
a0f0fff250474d5382084f72616c2d42 (Data)
properties read, write
value 00000000 | ''
a0f0fff350474d5382084f72616c2d42 (Auth)
properties read, write
value 00 | ''
a0f0fff450474d5382084f72616c2d42 (Secret)
properties read, write
value 00000000 | ''
Service a0f0ff0050474d5382084f72616c2d42
a0f0ff0150474d5382084f72616c2d42 (Handle ID)
properties read
value 00000000 | ''
a0f0ff0250474d5382084f72616c2d42 (Handle Type)
properties read
value 01 | ''
a0f0ff0350474d5382084f72616c2d42 (User Account)
properties read
value 01 | ''
a0f0ff0450474d5382084f72616c2d42 (Device State)
properties read, notify
value 0200 | ''
a0f0ff0550474d5382084f72616c2d42 (Battery Level)
properties read, notify
value 34 | '4'
a0f0ff0650474d5382084f72616c2d42 (Button State)
properties read, notify
value 00000000 | ''
a0f0ff0750474d5382084f72616c2d42 (Brushing Mode)
properties read, notify
value 01 | ''
a0f0ff0850474d5382084f72616c2d42 (Brushing Time)
properties read, notify
value 0000 | ''
a0f0ff0950474d5382084f72616c2d42 (Quadrant)
properties read, notify
value 00 | ''
a0f0ff0a50474d5382084f72616c2d42 (Smiley)
properties read, notify
value 00 | ''
a0f0ff0b50474d5382084f72616c2d42 (Pressure Sensor)
properties read, notify
value 00 | ''
a0f0ff0c50474d5382084f72616c2d42 (Cache)
properties read, write, notify
value | ''
Service a0f0ff2050474d5382084f72616c2d42
a0f0ff2150474d5382084f72616c2d42 (Status)
properties read, write, notify
value 8200 | ''
a0f0ff2250474d5382084f72616c2d42 (RTC)
properties read, write
value 8d15ac21 | '
a0f0ff2350474d5382084f72616c2d42 (Timezone)
properties read, write
value a7 | '''
a0f0ff2450474d5382084f72616c2d42 (Brushing Timer)
properties read, write
value 0f | ''
a0f0ff2550474d5382084f72616c2d42 (Brushing Modes)
properties read, write
value 0105020403060000 | ''
a0f0ff2650474d5382084f72616c2d42 (Quadrant Times)
properties read, write
value 1e001e001e001e000000000000000000 | ''
a0f0ff2750474d5382084f72616c2d42 (Tongue Time)
properties read, write
value 00 | ''
a0f0ff2850474d5382084f72616c2d42 (Pressure)
properties read, write
value 03 | ''
a0f0ff2950474d5382084f72616c2d42 (Data)
properties read
value 4ef1a721800002010000046478801d00 | 'Nq'!dx'
a0f0ff2a50474d5382084f72616c2d42 (Flight Mode)
properties read, write
value 00 | ''
Program to hack Bluetooth Low Energy (BLE) from a mobile phone
Since all modern phones have Bluetooth, you can use applications for working with Bluetooth Low Energy (BLE) surrounding devices on the phone.
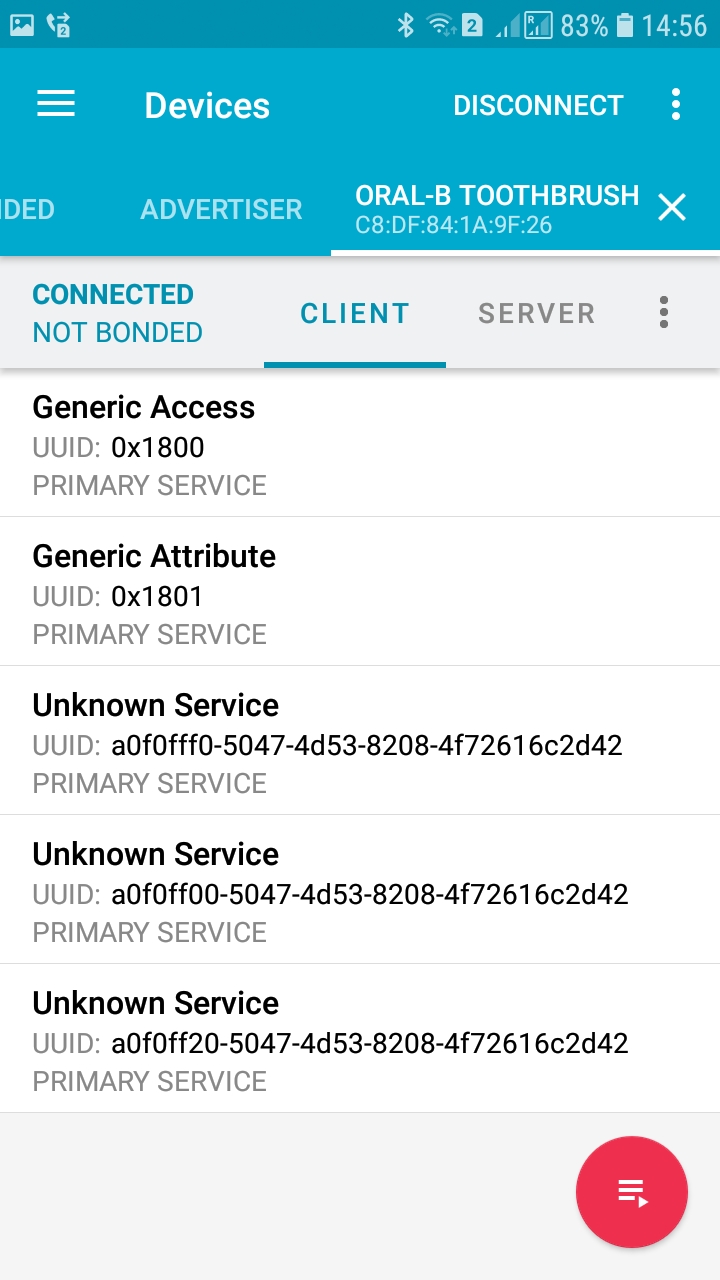
An example of such an application is nRF Connect, a free program for Android that can scan for BLE devices, connect to them and change the value of characteristics. The program supports macros and other advanced functions.
View device services:
View characteristics' properties:
Editing characteristic values:
Working with Bluetooth Low Energy (BLE) on Linux
Of course, on Linux, you can work with devices that support BLE directly without programs such as Bettercap.
Unfortunately, this aspect is rather confusing. In Debian and its derivatives, Bluetooth Low Energy software is compiled in the bluez package. In Arch Linux and its derivatives, the bluez package is also available, but the utilities that interest us are included in the bluez-utils package. But this is not the biggest problem.
After an update of the bluez utilities, the authors suddenly declared many important programs as “deprecated”, they are:
- gatttool
- hciattach
- hciconfig
- hcidump
- hcitool
- rfcomm
- ciptool
- sdptool
Amazingly, there were no full replacements for them. The things are getting worse by the lack of normal documentation and even help summary on the programs.
The following replacement table was compiled:
| Deprecated tool | Most likely replacement |
|---|---|
| gatttool | btgatt-client, D-Bus Gatt API |
| hciattach | btattach |
| hciconfig | btmgmt (and bluetoothctl?) |
| hcidump | btmon (and btsnoop) |
| hcitool | missing, D-Bus Device API available |
| rfcomm | missing, implement with D-Bus Profile1 API? |
| ciptool | |
| sdptool | missing, functionality seems to be scattered over different D-Bus objects: Profile, Advertising, and the UUIDs arrays in device and adapter. |
The words “missing” do not inspire confidence. For this reason, for Debian and its derivatives, this package compiles with the --enable-deprecated flag, and on Arch Linux, in addition to the bluez-utils package available in standard repositories, AUR has the bluez-utils-compat package, which also includes legacy tools.
In relatively recent instructions, the following utilities are used to interact with Bluetooth Low Energy:
- hcitool
- gatttool
Since they are deprecated and one day they will be permanently deleted, consider a few simple options for using their replacements to search for BLE devices and get data from them.
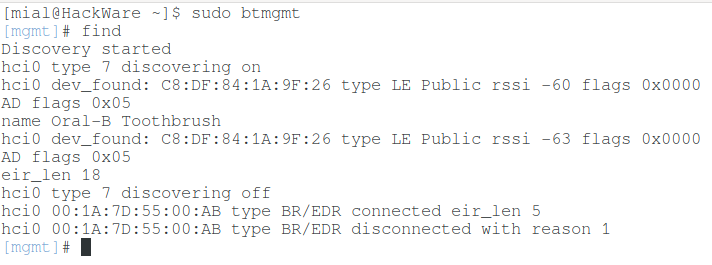
If you run the btmgmt program:
sudo btmgmt
And in it execute the command:
find
Then it will list the detected devices:
Both BLE and regular Bluetooth devices will be displayed.
Another program:
sudo bluetoothctl
It can also search for BLE devices by entering:
scan on
Using the connect command, you can connect to the device, for this you need to specify its MAC address:
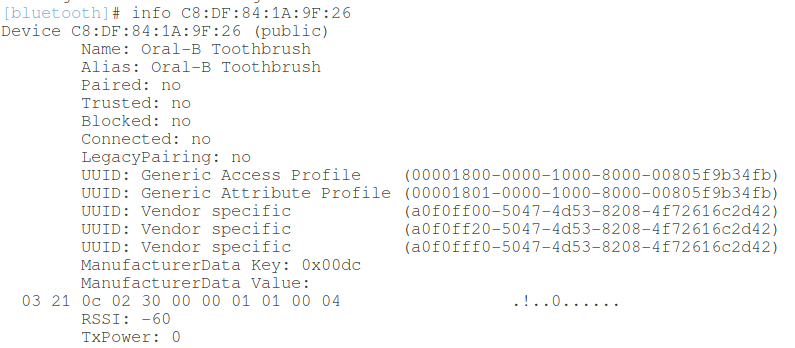
connect C8:DF:84:1A:9F:26
Device Information:
info C8:DF:84:1A:9F:26
If you go to the GATT menu:
menu gatt
Then you can get a list of characteristics:
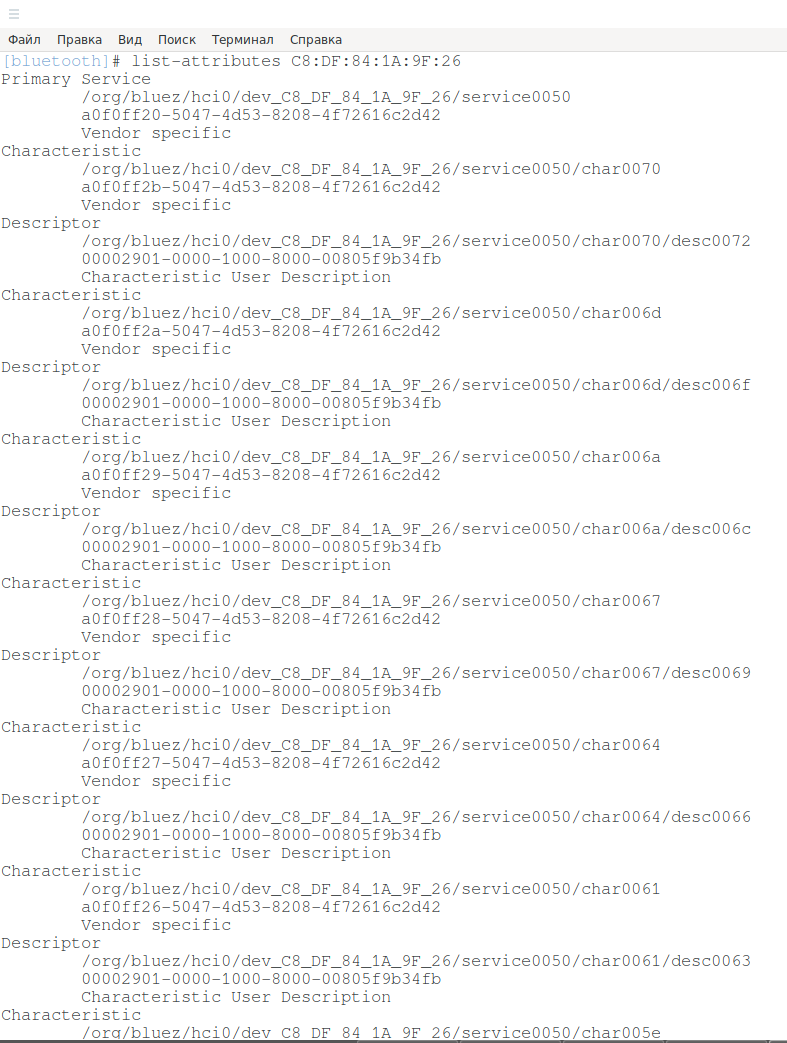
list-attributes C8:DF:84:1A:9F:26
And also overwrite the characteristics of the device.
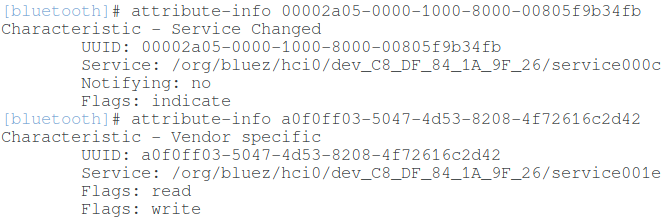
For information on individual characteristics:
attribute-info 00002a05-0000-1000-8000-00805f9b34fb attribute-info a0f0ff03-5047-4d53-8208-4f72616c2d42
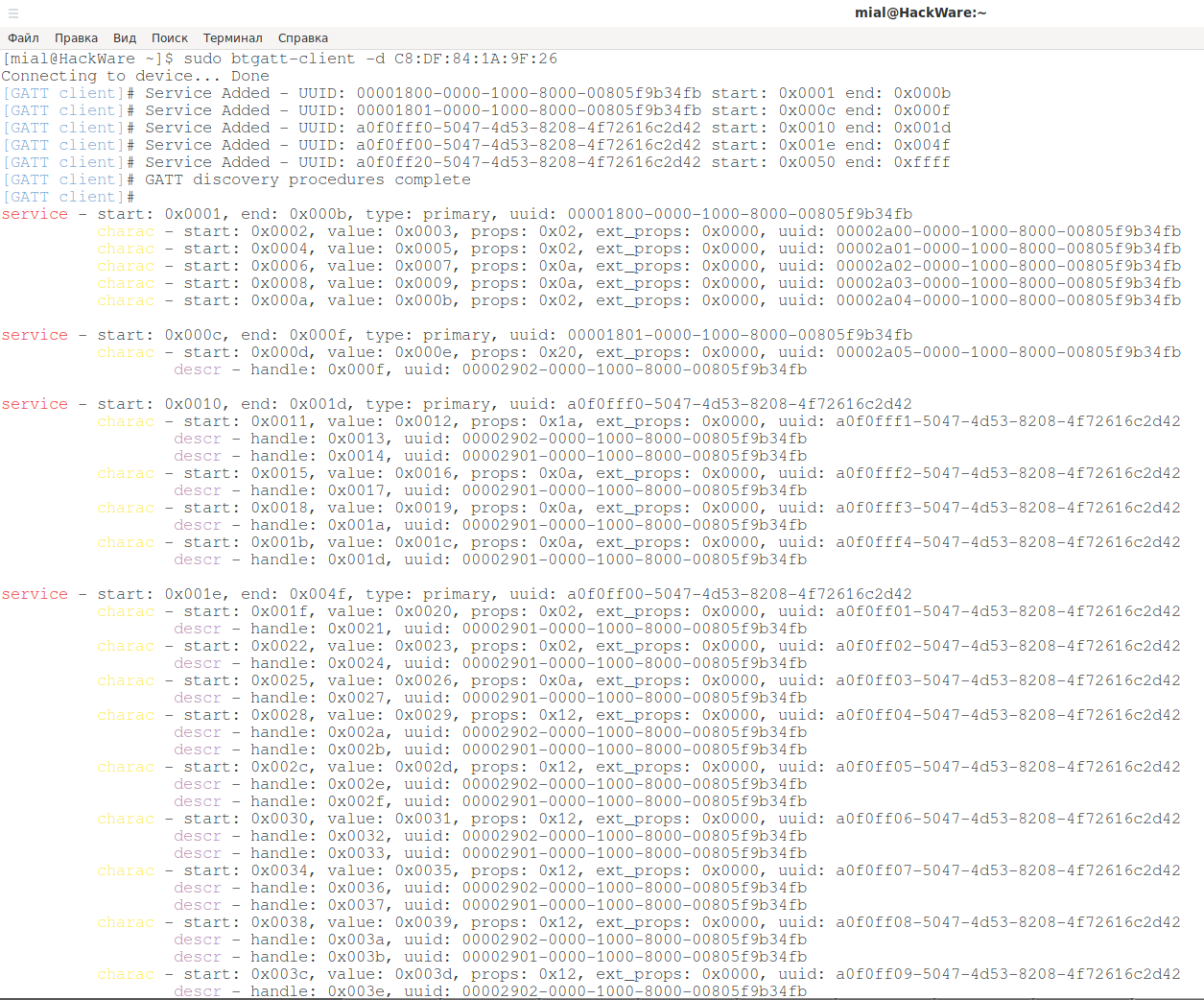
Another program that immediately displays all the characteristics of the device is btgatt-client. For example, make a connection and see the characteristics of a device with MAC C8:DF:84:1A:9F:26:
sudo btgatt-client -d C8:DF:84:1A:9F:26
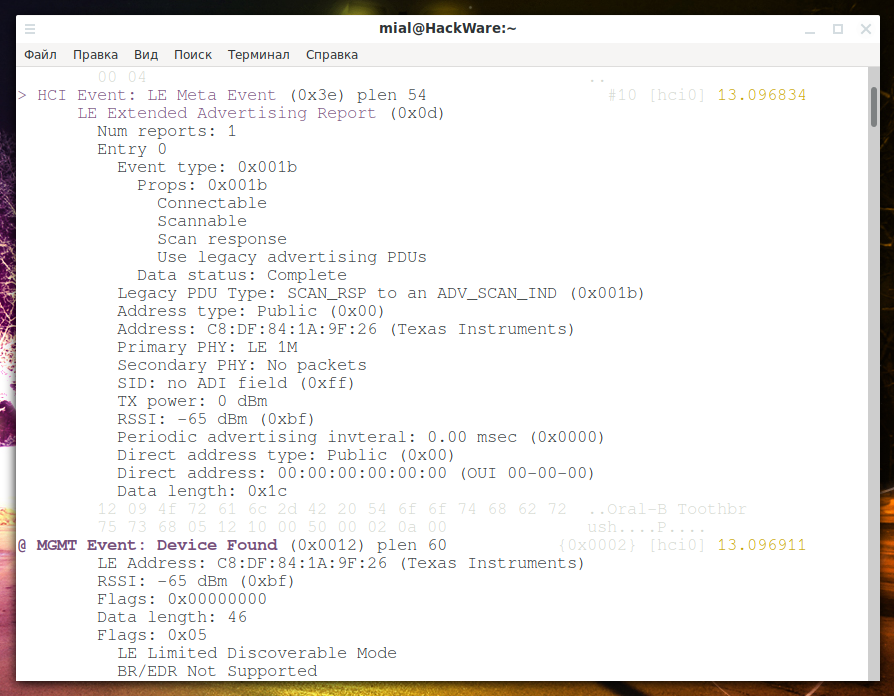
In addition to the reviewed programs, in a separate console, you can run Bluetooth monitor:
sudo btmon
As befits a monitor program, it will display a lot of information about what is happening with Bluetooth and about detected devices.
Conclusion
Linux system utilities for working with Bluetooth deserve a closer look – with their help you can find out more detailed information about your system and fine-tune the Bluetooth adapter.
They can also be used to implement scanners of BLE and Bluetooth devices and/or write or adapt fuzzers to find out the purpose of the characteristics of BLE devices. Therefore, it is possible that in one of the following articles, programs for working with BLE will be discussed in more detail.
Bibliography
- https://blog.attify.com/the-practical-guide-to-hacking-bluetooth-low-energy/ ( http://archive.fo/zfJwZ#selection-1419.0-1419.8 )
- https://www.evilsocket.net/2017/09/23/This-is-not-a-post-about-BLE-introducing-BLEAH/
- http://archive.fo/r776M
- https://wiki.archlinux.org/index.php/Bluetooth#Troubleshooting
- https://bbs.archlinux.org/viewtopic.php?id=223884
- https://www.esp-forum.de/index.php/forum/hacking-und-tear-down/101-oral-b-zahnbuerste-auslesen-bluetooth-4-1-low-ene
Related articles:
- Automatic handshake and PMKID capture from all access points (95.6%)
- WiFi-autopwner: script to automate searching and auditing Wi-Fi networks with weak security (58.7%)
- Rogue Wi-Fi AP with mitmAP: setting up and data analysis (58.7%)
- Mass and endless handshake capture from all Access Points in a range (58.7%)
- How to perform selective jamming of Wi-Fi networks and clients (DoS attack on individual access points / clients) (58.7%)
- How to create a Rogue Access Point (connected to the Internet through Tor) (RANDOM - 58.7%)


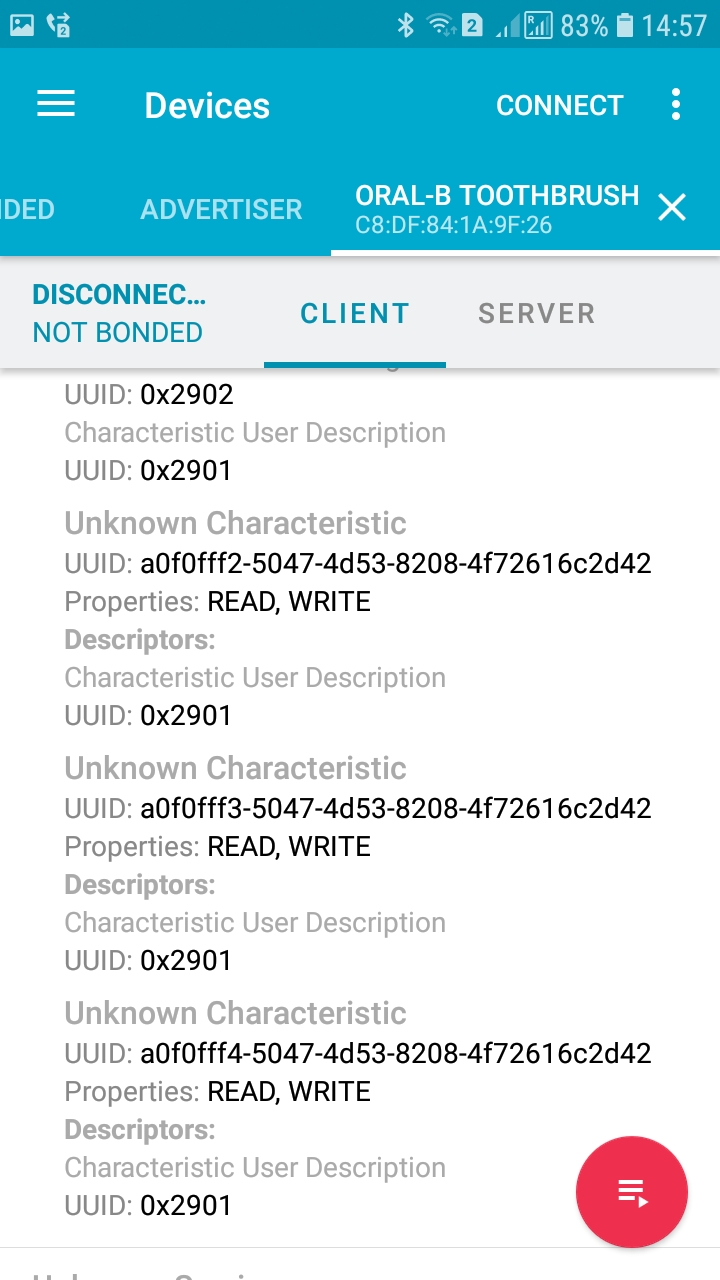
Hi, I was using bettercap to enumerate a pulse oximeter and trying write value on but not sure what will be the value here, i have attached an image of my captured data:
You said, "To achieve aims, it is necessary to know what the characteristic IDs mean.". But how to figure out the characteristic IDs meaning?
Thanks. I would really appreciate any response.
love your writeup, good research, a lot of information in a clear explaination that is easy to grasp.